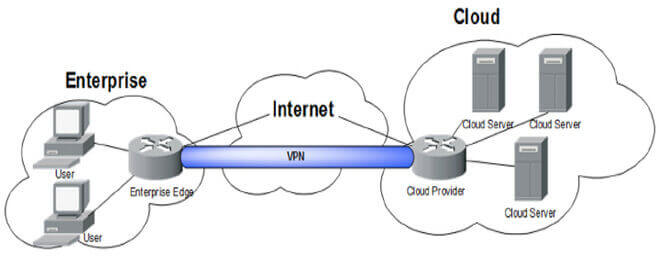
How a VPN works? The construction of a VPN server diagram is our topics today.
If you want to continue utilizing VPNs as your main method of online security, you must be able to easily extend your network.
VPNs provide users anonymity and encryption. This article is for you if you want to design a VPN server diagram or find out more about how this kind of technology works.
This clever technology has lately been widely utilized online, and many individuals use it to conceal their identities from websites they visit as well as from their social media accounts.
Although the SSG is often referred to as a proxy, Hidemyass.com is the most widely used one online.
Anyone may use this wonderful proxy server for security reasons since it can unblock any website you wish to access.
It is helpful for getting around your ISP’s filtering mechanisms while also protecting your online identity. Public VPNs are far more secure since they don’t record use or traffic, as we already said.
What is a VPN?
Employees may work remotely, access company resources, and send data securely thanks to VPN technology. By encrypting user traffic and routing it via a middle server, VPNs safeguard users’ privacy. The network is accessible to employees from any location in the globe.
We’ll demonstrate how to create a simple VPN server diagram in this blog article. In order to get started, you must first set up a virtual network in your Hyper-V environment.
Your VPN server may be built on top of this virtual network. Make two virtual machines next; one will operate as the VPN server and the other as the gateway (or client) computer.
The virtual VPN server machine should then have the Hyper-V role installed. This is simple to achieve since the Hyper-V role contains tools for building and maintaining virtual networks.
Finally, set up a secure connection between the gateway virtual machine and the VPN server virtual machine.
On Windows or Linux, how to configure a VPN server diagram
On Windows or Linux, setting up a VPN server is simple. All you need is a VPN client, an IP address for your VPN server, and a server operating system. A virtual private network (VPN) is another tool you may use to safeguard your online data.
To create a Linux or Windows VPN server:
- Launch the server operating system and establish an Internet connection.
- Type “ipconfig” into the command prompt or terminal window. Your current IP address and other details will be shown.
- To display all of your computer’s active connections, use “nets tat -a.” You can see which applications use the most bandwidth. When setting up your VPN server, you may use this information to choose which apps to deactivate.
- Enter “route.” To add the IP address of your computer’s default route to the routing table, use the command add default. The PC may use this to access the Internet from any location inside your home network.
- Enter “to make sure your computer can connect to the network’s default router. Instead, enter “route”
Creating a VPN server on Mac OS X
On Mac OS X, setting up a VPN server is simple and takes little time. This guide will demonstrate how to install an external VPN provider as well as how to configure a VPN server on your computer using the built-in VPN client.
A VPN server diagram has to include the following components:
- At least two computers that will operate as the VPN server (s).
- A network link connecting the computers.
- Each computer system has an IP address.
- Every computer system has VPN software installed.
- A VPN tunnel is established between the two computers.
- VPN server configurations set up on every computer system.
You must choose the kinds of networks you wish to connect to before you can design a VPN server diagram. A VPN server diagram is not necessary if you simply wish to connect to a single network.
You need a VPN server diagram if you wish to connect to many networks. You must decide which machines will function as your VPN servers after determining the sort of network you will use.
A network connection tester like sleep or Wireshark is the ideal tool to use for this.
An IP address is the next thing any computer system needs. Using a DHCP service or a network address translator (NAP), you may get these addresses. Finally, you must setup each VPN with the required software and settings.
What advantages come with utilizing a VPN?
A VPN is a fantastic tool for online privacy and security protection. VPNs help keep your data anonymous by encrypting your transmission. Here are a few advantages of utilizing a VPN:
– Protect Your Privacy: Using a VPN encrypts your internet traffic and shields it from prying eyes. This protects the privacy of your browser history and prevents third parties from monitoring your online activities.
– Protect Your Data: When you use a VPN, cybercriminals and hackers cannot access your data. You may prevent theft and unwanted access to your personal information by connecting to a secure VPN server.
– Maintain Your Online Anonymity: When you use a VPN, your online identity is protected. Your identity is kept secret from others, making it simpler to avoid being followed online.
– Prevent ISP Throttling: Many ISPs prohibit or slow certain traffic categories in accordance with their own policy determinations. You may get around these limitations and use the whole bandwidth of your internet connection by utilizing a VPN.
Final thoughts
You will learn how to create a VPN server diagram in this tutorial. Anyone who wishes to safeguard their online activity and guard their data against theft or unwanted access has to master this ability.
Understanding how a VPN works can help you build your own secure network that will keep your private data safe. Therefore, go ahead and begin creating your own VPN server diagram! Basic VPN Diagrams.
You want to draw a VPN diagram, then. Great! Because you are now familiar with how the various components of a VPN operate, you are halfway there. We must first take into account all of the potential places where a user may be found.
For instance, both a worker in the office and a worker on vacation at home need a VPN connection. This calls for consideration of the locations of these users who will be using the VPN and the level of protection those locations will provide.
There may also be a place here for things like firewalls, fortifications, and general security checks.
Hope you have got a clear idea about the construction of a VPN server diagram. Now its time to share your thoughts and experience about the VPN server diagram in the comment section bellow.
Recommended for you:
Why should you use Ubuntu for server management?
What are the 9 best iPad for you?
What is DevOps? All you need to know about DevOps