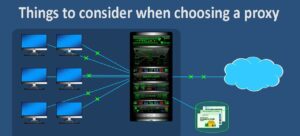
Virtual private networks (VPNs) are becoming increasingly popular as more people seek to protect their online privacy and security.
But even though VPNs offer a lot of advantages, there are still many misconceptions about how they work and what features they offer. Here are eight exciting VPN myths.
What are the 8 myths of virtual private networks?
Here are the 8 interesting myths of virtual private networks.
Myth 1: VPNs Slow Down Your Connection Speed
The truth is that using a quality VPN service can actually improve your connection speed rather than slowing it down.
Any slowdown in the internet is usually because the server you’re connected to is far away, or because the number of users connected simultaneously is too high.
You should, therefore, choose a VPN provider with many servers close to your home.
As a side note, there are some instances when VPNs do not work on specific systems.
For example, if there is a VPN not working on Mac, double-check whether the provider indicates their service compatibility with various devices and operating systems.
Myth 2: You Don’t Need A VPN If You Are Connected To A Secure Network
This myth exists mainly because some people believe that if they connect to a secure network, such as in an office or at home, then the data transmitted is already encrypted and protected from hackers.
The truth, however, is that data can be intercepted and decrypted even on these networks if someone has access to the network itself.
A VPN provides an additional layer of security for data transmitted over public or private networks by encrypting it through authentication protocols.
Myth 3: It’s Not Necessary To Use A Paid Service Because There Are Free Ones Available
Although there are free services available, these often have limited features and slower speeds compared to paid services due to overcrowded servers and other factors such as advertising being displayed when using the service.
Free services may also require you to provide personal information in order to use them (such as your email address).
Paid services generally provide:
- Better speeds.
- More reliable connections.
- Improved customer support.
- Greater protection against cyber threats such as malware or identity theft.
Myth 4: All Services Offer The Same Features
Although most services will have similar features, there can be differences between different providers which could make one service better than another depending on your requirements.
Common features include unlimited bandwidth, unlimited device connections, military-grade encryption and no logs policy but some may offer additional features such as dedicated IP addresses or split tunneling capabilities.
It’s important to understand what each feature does before choosing a provider so you get the most out of your subscription plan.
Myth 5: All Services Offer Global Access To Servers
Though most providers advertise global coverage, this isn’t always the case; for example, some providers may only have servers located in certain countries, meaning you won’t be able to access region-specific content from other countries unless you switch providers or manually configure your connection settings every time you want to change countries/regions (which isn’t ideal).
Always check which countries a provider offers servers in before signing up for any plans – ideally, they should have servers located all around the world so you do not have to experience any restrictions based on your location when trying to check online content from overseas websites/services, etc.
Myth 6: You Don’t Need Multiple Accounts With The Same Service Provider For Different Devices
Most quality services will allow up to five devices per account, as long as they are all being used by one user;
However, this does not mean that having multiple accounts with the same provider is redundant – it is actually advisable if you use different types of devices regularly (e.g., phones and tablets versus laptops and desktops).
Different devices require different configuration settings, which can save time if each device has its own account.
Just make sure that each account has different logins so that each device isn’t sharing data with another device connected under the same username and password combination.
Myth 7: All Services Have The Same Logging Policies
Logging policies vary greatly among different companies, so it is important to understand exactly what kind of information each provider stores about its users.
Otherwise, you could find yourself unknowingly agreeing to let them store details about your browsing activity, which undermines why people use a service.
Generally speaking, most good-quality providers will have strict no-log policies in place, meaning none of your activity is stored or shared with anyone else.
This helps ensure maximum privacy and anonymity while using their services.
Myth 8: You Can Use A VPN To Access Dark Web Sites And Services
Using a VPN alone will not give you entry to the deep web and services—these require more than just connecting through a secure tunnel.
An anonymous IP address can help, as many dark websites do not accept traffic from known sources such as Internet Service Providers (ISPs).
Most dark web sites also require special software like the TOR browser, which enables anonymous communication over public networks before allowing any user access to them – without going into too much technical detail, suffice it to say that using just a regular VPN won’t cut it when attempting to reach “the hidden internet”.
See also:
Best 32 VPN affiliate programs to earn high commission
Construction of a VPN server diagram
Best 10 techniques to speed up internet connection
15 most important cyber security tips for business
How to setup a proxy server? 3 main types of proxy server and setup process
What is the Advanced Encryption Standard (AES)? All You Need to Know about AES