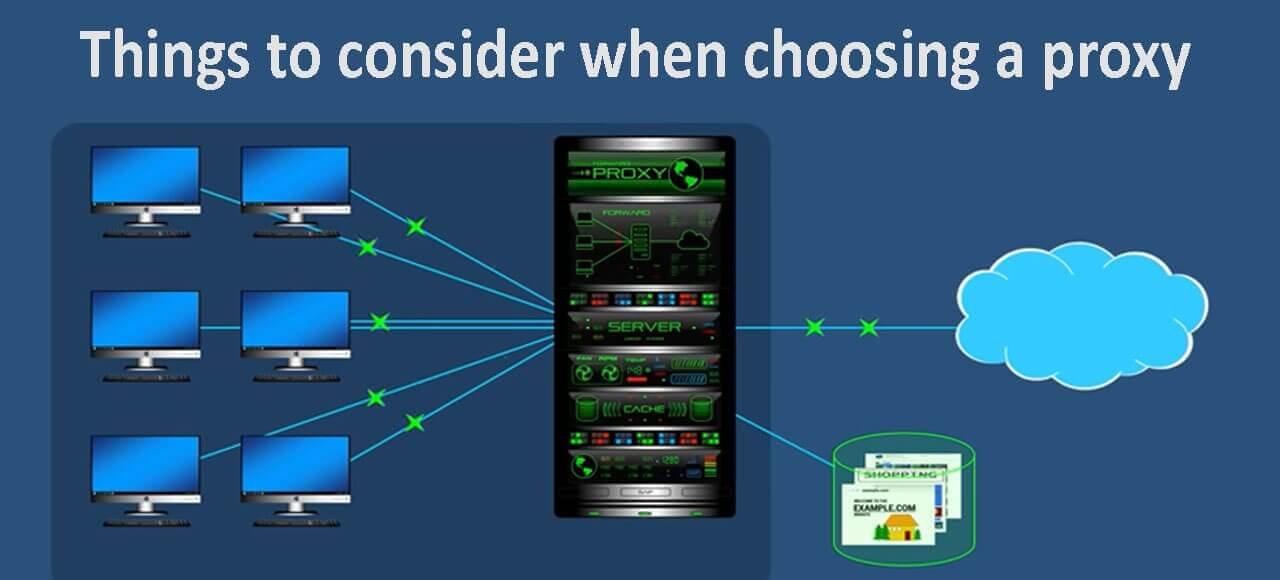
There’s a lot of things to consider when choosing a proxy and here we will dive into some key consideration before choosing your proxy.
A proxy, in the context of computer networking and the internet, is an intermediary server or computer that acts as a gateway between a user’s device and the destination server or website the user wants to access.
When you use a proxy, your internet requests (e.g., for a website or a file) do not go directly to the target server.
Instead, they are first routed through the proxy server, which then forwards your request to the target server and returns the response to your device.
Proxies can hide your IP address, making it more challenging for websites and services to track your online activities. This is often used for online privacy and security.
Proxies can be used to filter or block specific types of content, such as restricting access to certain websites or content categories on a network.
Proxies can be configured to restrict or control access to specific websites or online resources within an organization or network.
Some proxies can cache web content, making it faster to load frequently accessed resources by storing copies of those resources.
Now let’s see the 15 most important things to consider when choosing a proxy.
Things to consider when choosing a proxy
15 Things to consider when choosing a proxy are given bellow. The consideration fact may vary according to your need. So read carefully before choosing your own proxy.
1. Types of the proxy
There are different types of proxies, including HTTP, HTTPS, SOCKS, transparent, anonymous and many more. The type you choose depends on your intended use case.
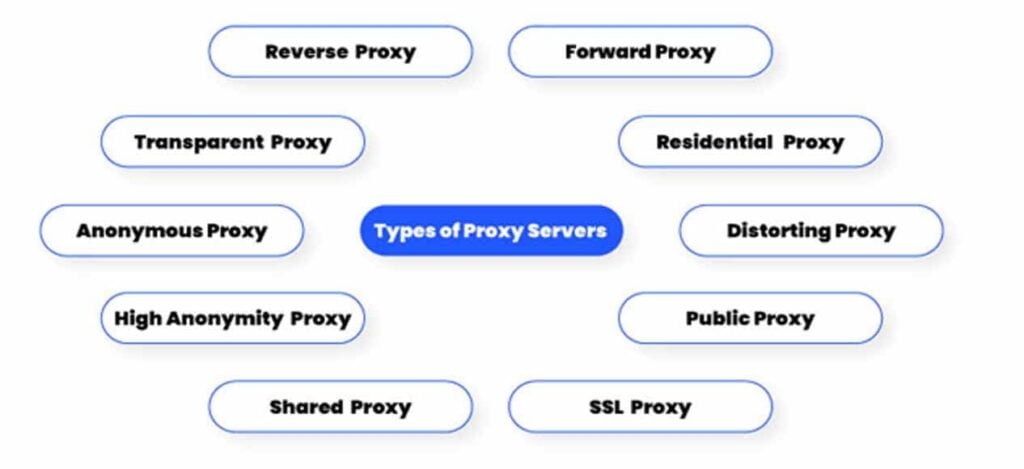
HTTP proxies are suitable for web browsing, while SOCKS proxies are more versatile and can handle various types of traffic.
Transparent Proxies reveal your IP address to the target server but are used for content filtering while anonymous proxies hide your IP address but can still be detected as proxies.
If you need some degree of anonymity but don’t require the highest level, anonymous proxies can be a good choice. They can hide your IP address, making it more challenging for websites to track your online activities.
At last there is Elite proxies which provide the highest level of anonymity, making it difficult for websites to detect that you are using a proxy.
It’s important to note that even with elite proxies, some websites and services may employ more advanced methods to detect proxy usage.
Additionally, the level of anonymity is not the only factor to consider when choosing a proxy. Factors like speed, reliability, and the provider’s reputation also play a significant role in your proxy selection.
2. Anonymity Level of the proxy
The anonymity level of a proxy server refers to how well it hides your IP address and other identifying information when you use it to access websites and online services.
Proxies vary in terms of the anonymity they provide. Transparent proxies reveal your IP address, while anonymous and elite proxies hide your IP address, offering a higher level of anonymity.
There are different levels of anonymity associated with various types of proxy servers such as the transparent proxies do not hide your IP address.
When you use a transparent proxy, the target server can still see your real IP address. They are often used for content filtering and caching but provide little to no anonymity.
Anonymous Proxies hide your IP address from the target server, making it more difficult for websites to identify you.
However, some websites and services may still detect that you are using a proxy. These proxies provide a moderate level of anonymity.
On the other hand Elite Proxies (High-Anonymous Proxies) offer the highest level of anonymity. They not only hide your IP address but also do not reveal that you are using a proxy.
For websites and online services, it appears as though the request is coming directly from the proxy server, enhancing your online privacy and anonymity.
3. Purpose of your choosing the proxy
Determine why you need a proxy. Is it for accessing region-restricted content, enhancing online privacy, or web scraping? Your use case will influence the type of proxy you choose.
The best proxy for a specific purpose can vary depending on your exact needs and use case. Here are some common purposes and the best proxy for that.
Web Browsing and General Online Privacy: For this you should choose Elite (High-Anonymous) Proxies because they provide the highest level of anonymity and are suitable for protecting your online identity and location while browsing the web. They hide your IP address effectively.
Accessing Geo-Restricted Content: For this purpose you should choose Residential Proxies as they use IP addresses associated with real residential internet users.
They are ideal for accessing geo-restricted content, as they appear as though they’re coming from real users in specific regions.
Web Scraping and Data Collection: You should choose Datacenter Proxies for this purpose as they are fast and reliable, making them suitable for web scraping and data collection tasks. They are typically less expensive than residential proxies.
Content Filtering and Censorship Bypass: Choose SOCKS Proxies as they are versatile and can be used for various types of traffic, including bypassing content filters or censorship in certain situations. They can handle non-web traffic, which is common in such cases.
Improved Online Security: You should choose Proxy Servers with Security Features. For example if you’re looking to enhance your online security, consider using proxies that include additional security features like web filtering, antivirus scanning, and firewall capabilities.
SEO and Online Marketing: You should consider Residential Proxies or Rotating Proxies For tasks like SEO monitoring, competitor analysis, and online marketing, using residential or rotating proxies can help you gather data from various locations without getting blocked.
Torrenting and P2P File Sharing: Try to choose SOCKS or VPN Proxies. While it’s important to note that many countries and ISPs restrict torrenting, if you are in a location where it is allowed, SOCKS or VPN proxies can provide anonymity and security for torrenting.
Gaming and Reducing Latency: Gaming Proxies may be best as some gaming proxies are optimized to reduce latency and provide a more stable gaming experience.
However, be cautious when using proxies in online gaming, as some games have terms of service that prohibit their use.
Stress Testing and Network Security: Choose Datacenter Proxies because datacenter proxies are often used for stress testing and network security purposes. They are cost-effective and can handle high loads of traffic.
Now let’s try to summarized that which proxies is best for which purpose:
| Purpose Of Use | Best Proxy Type |
| Web Browsing and General Online Privacy | Elite (High-Anonymous) Proxies |
| Accessing Geo-Restricted Content | Residential Proxies |
| Web Scraping and Data Collection | Datacenter Proxies |
| Content Filtering and Censorship Bypass | SOCKS Proxies |
| Improved Online Security | Proxy Servers with Security Features |
| SEO and Online Marketing | Residential Proxies or Rotating Proxies |
| Torrenting and P2P File Sharing | SOCKS or VPN Proxies |
| Gaming and Reducing Latency | Gaming Proxies |
| Stress Testing and Network Security | Datacenter Proxies |
4. Location and Geo-Targeting
If you need to access content restricted to a specific geographical location, choose a proxy server in that region. This is important for activities like accessing geo-blocked content or performing SEO tasks.
Location and geo-targeting are important considerations when choosing a proxy for some other reasons too.
For example many websites and online services restrict access to content based on the geographical location of the user. For example, streaming platforms often offer different content libraries in different countries.
By using a proxy server located in the desired region, you can access content that might otherwise be restricted in your actual location.
This is particularly useful for accessing region-specific streaming services, news, or other geographically restricted content.
If you are involved in search engine optimization (SEO) or online marketing, you may need to view search engine results or collect data from specific geographic regions.
Using a proxy with a server in the target location allows you to see localized search results and gather accurate data for local SEO efforts.
Developers and quality assurance professionals often need to test how websites or applications perform in different regions.
Using proxies with servers in those regions helps them identify and address location-specific issues and ensure that the product works as expected for users worldwide.
For online privacy and security, using a proxy server located in a different region can help mask your actual location and provide an additional layer of privacy.
This can be important for individuals in countries with strict internet censorship or surveillance.
Content delivery networks (CDNs) use geolocation to serve content from servers located closer to the user. By selecting a proxy server in proximity to a CDN server, you can improve content delivery speed and website performance.
Some online activities are subject to different regulations or laws depending on the geographic location of the user. By using a proxy server in a different region, you can navigate these restrictions and regulations.
Market researchers and data analysts may require data from various regions to gain insights into market trends and customer behavior. Proxies with different geographical locations enable them to collect region-specific data efficiently.
When choosing a proxy for location-specific needs, it’s essential to select a proxy server that offers servers in the region you are targeting.
Additionally, consider factors like speed, reliability, and the proxy provider’s reputation to ensure that your proxy server meets your requirements for accurate and efficient geo-targeting.
5. Speed and reliability
The proxy’s speed and reliability are crucial. Slow proxies can hinder your internet experience, and unreliable proxies may disconnect frequently.
Datacenter proxy may be the best choice for you if speed is your primary concern as they tend to be faster than the other proxies.
Speed is an important consideration when choosing a proxy for several reasons including user experience, efficiency, productivity, SEO, marketing as well as data integrity and many more.
A fast proxy server ensures a better overall user experience. Slow proxies can lead to frustratingly long loading times for websites and applications, making it less enjoyable for users.
Speed is crucial when performing tasks that involve data retrieval, such as web scraping, content crawling, and automated data processing. A fast proxy allows you to complete tasks more quickly and efficiently.
For businesses and organizations, time is money. Slow proxies can lead to decreased productivity and increased wait times for employees who rely on the internet for their work.
Again if you’re using a proxy for streaming or downloading purposes, speed is essential. Slow proxies may result in buffering issues when streaming video or extended download times for files.
Gamers who use proxies for reducing latency or accessing region-restricted game content require fast connections to maintain smooth gameplay. Slow proxies can lead to lag and gameplay disruptions.
In SEO and online marketing, tasks like monitoring website rankings, competitor analysis, and collecting data from search engines require speed. Slow proxies may lead to inaccurate or delayed data.
E-commerce websites and applications depend on a responsive user experience. Slow proxies can deter potential customers and lead to reduced sales.
When web scraping or collecting data, the speed of your proxy can impact the integrity of the data. Slow proxies may result in incomplete or outdated information.
Fast proxies are less likely to experience downtime or disconnections, ensuring a more reliable and consistent connection to the internet and the services you rely on.
Speed is essential for content delivery networks (CDNs) that use proxy servers. A fast proxy ensures efficient content distribution and reduces latency for end-users.
However, from the above discussion we can say that when choosing a proxy, it’s crucial to consider the balance between speed and other factors, such as security, reliability, and anonymity.
Some proxy types, like datacenter proxies, are known for their speed, while others, like residential proxies, offer more anonymity but may be slightly slower.
Select the proxy that best aligns with your specific needs and use case to ensure an optimal online experience.
6. Security of the proxy
Ensure the proxy server is secure and not compromised. Using an unsecured proxy can expose your data and compromise your online privacy.
Security is a critical consideration when choosing a proxy for several important reasons including:
- Protection from Cyber Threats: Proxies can act as a barrier between your device and the internet, filtering and inspecting incoming and outgoing traffic.
- A secure proxy can help protect you from various online threats, including malware, viruses, and phishing attacks, by detecting and blocking malicious content.
- Privacy and Anonymity: One of the primary reasons people use proxies is to enhance online privacy and anonymity.
- A secure proxy can help safeguard your identity and location by masking your IP address, making it more difficult for websites and online services to track your online activities.
- Data Encryption: Some proxies, like HTTPS and SOCKS proxies, support encryption. When data is transmitted through an encrypted proxy, it is more secure and less susceptible to interception by malicious third parties, adding an extra layer of data protection.
- Content Filtering and Access Control: In business and organizational settings, proxies are often used for content filtering and access control.
- A secure proxy can enforce policies that restrict access to inappropriate or malicious websites, helping to maintain a safe and compliant online environment.
- Network Security: Proxies can be integrated into a broader network security strategy. They can filter out harmful traffic and protect internal network resources from external threats, such as distributed denial-of-service (DDoS) attacks.
- Protection from Monitoring and Surveillance: In regions where internet surveillance is a concern, secure proxies can help users circumvent monitoring and censorship efforts by encrypting their internet traffic and making it difficult for government or third parties to intercept and analyze their data.
- Compliance and Legal Requirements: Some industries and organizations have legal and compliance requirements related to data protection and security.
- Protection of Sensitive Information: If you’re accessing or transmitting sensitive information, such as financial data or personal details, a secure proxy helps ensure that this information is kept confidential and safe from unauthorized access.
- Preventing Data Leaks: Proxies can help prevent data leaks by controlling and monitoring the flow of data to and from your network. They can restrict unauthorized data transfers and ensure that sensitive information doesn’t leave your network.
7. Logging Policy of the proxy
Check the proxy provider’s logging policy. Some proxies log your activity, while others offer a “no-log” or “zero-log” policy. For privacy, it’s often best to choose a provider with minimal or no logging.
When evaluating the logging policy of a proxy provider, look for the following information:
- What data is collected?
- How long is the data retained?
- How is the collected data used?
- Is the data shared with third parties?
- What security measures are in place to protect the stored data?
A reputable proxy provider should be transparent about their logging policy, and it’s advisable to choose one that aligns with your privacy and security needs.
If privacy and anonymity are your primary concerns, prioritize providers with strict no-log policies.
8. Authentication of proxy
If you require additional security, consider proxies that offer user authentication. This ensures that only authorized users can access the proxy.
Authentication is an important feature when choosing a proxy for several reasons like:
- Access control;
- Security;
- User accountability;
- Protecting sensitive data;
- Regulatory compliance;
- Customization;
- Preventing unauthorized use;
- Privacy and anonymity;
- Preventing abuse etc.
When choosing a proxy with authentication, you should consider the following:
- Type of Authentication: There are different methods of authentication, including username/password, IP-based, and token-based authentication. Choose the method that best suits your needs and security requirements.
- Management and Configuration: Ensure that the proxy server and its authentication mechanism are easy to manage and configure. User-friendly administration tools can simplify the process of setting up and managing user accounts.
- Scalability: If you expect to have multiple users or need to scale your proxy service, ensure that the authentication system can handle your requirements and grow with your needs.
- Security Measures: Implement additional security measures, such as two-factor authentication (2FA), to enhance the security of the authentication process.
9. Customer support
I think everyone of you know how important the customer support is. This is one of the most important things to consider when choosing a proxy.
A responsive and helpful customer support team can be invaluable, especially if you encounter technical issues or have questions about your proxy service.
So, don’t forget to check their customer support before choosing a proxy for you.
10. Scalability of the proxy
Consider whether the proxy service can scale to meet your needs. Some projects may require multiple proxies or frequent IP changes.
The scalability of a proxy is important for several reasons, particularly in organizations and businesses with growing or evolving needs:
- Meeting Increased Demand;
- Flexible Resource Allocation;
- Improved Performance;
- High Availability;
- Redundancy and Reliability;
- Customization and Optimization;
- Accommodating Growth;
- Cost Efficiency;
- Geographical Expansion;
- Security and Load Balancing;
- Adaptation to Changing Technology;
- Compliance and Regulatory Requirements;
The importance of scalability becomes apparent when an organization experiences increased traffic, user demands, and evolving business objectives.
Scalable proxy solutions are designed to grow and adapt with these changes, ensuring that the proxy infrastructure remains reliable, efficient, and capable of supporting the organization’s needs over time.
11. Reputation of the proxy
Research the reputation of the proxy provider. Look for reviews and feedback from other users to ensure you’re choosing a reputable service.
12. Trial period they provide
Some proxy providers offer a trial period or money-back guarantee. This allows you to test the service to see if it meets your needs before committing.
13. IP address quality they provide
Proxies that use IP addresses associated with spam and malicious activity must be avoided at all costs. These IPs are almost always guaranteed to get blocked.
14. Check the tools they provide
A best-in-class proxy service typically offers a range of tools and features to enhance its functionality and meet various user needs.
Some of the common tools and features you can expect from a high-quality proxy service include:
- User Authentication: Secure proxies often provide authentication mechanisms, allowing you to control who can access the proxy service and establish user-specific policies.
- Logging Control: The ability to control or disable logging of user activity is important for those seeking maximum privacy and anonymity.
- Anonymity Levels: Quality proxies offer different levels of anonymity, including elite (high-anonymous) and anonymous proxies that hide your IP address effectively.
- Geographical Location Selection: You can choose proxy servers in specific regions or countries to access geo-restricted content or simulate being in a different location.
- Data Encryption: Some proxies support encryption (e.g., HTTPS or SOCKS5 proxies), which is vital for securing data transmission and maintaining privacy.
- Traffic Filtering and Content Control: Content filtering and access control features allow you to restrict or allow access to specific websites, content categories, or domains.
- IP Rotation and Pool Management: Proxies with IP rotation features enable you to cycle through a pool of IP addresses, making it more challenging for websites to detect and block your activity.
- Load Balancing: Load balancing tools distribute internet traffic evenly across multiple proxy servers, enhancing performance and reliability.
- Caching: Caching capabilities improve website loading speeds and reduce server load by storing copies of frequently accessed content.
- Scalability: Scalable proxy solutions can handle increased traffic and adapt to changing user requirements as your needs evolve.
- IP Whitelisting and Blacklisting: You can configure whitelists and blacklists to control which IPs are allowed or denied access through the proxy.
- Customized Rules and Policies: Quality proxies allow you to create and customize rules and policies that suit your specific use case, whether it’s web scraping, content delivery, or network security.
- Integration with Tools and Services: Some proxies offer integration with popular tools and services, such as web scrapers, automation scripts, and SEO software.
- High Availability: To minimize downtime, the best proxies offer high availability configurations that ensure service continuity, even in the event of server failures.
- Real-Time Monitoring and Reporting: You can monitor proxy server performance and user activity in real-time, and generate reports for analysis and compliance purposes.
- Customer Support and Documentation: Access to responsive customer support and comprehensive documentation can help users resolve issues and maximize the value of the proxy service.
- API Access: API access allows developers to integrate proxy services directly into their applications or scripts for automated usage.
- Speed and Reliability: High-quality proxies are known for their speed and reliability, ensuring an efficient and uninterrupted internet experience.
When choosing a proxy service, it’s essential to assess which tools and features align with your specific requirements, whether you need enhanced security, privacy, content control, or performance optimization.
The best proxy service for you will depend on your use case and objectives.
15. Pricing of the proxy
Different proxy services have different pricing models. Compare costs and consider your budget when selecting a proxy service.
You may be charged for several purposes based on the amount of data transferred, per proxy or per use case.
So considering your budget is also an important things to consider when choosing a proxy.
Final thoughts
Choosing the right proxy server is crucial for achieving your online goals, whether it’s enhancing privacy, accessing geo-restricted content, or conducting web scraping.
Consider these factors and conduct thorough research to make an informed decision that aligns with your requirements.
Choosing the right proxy server involves considering your specific needs, whether it’s for enhanced privacy, security, accessing geo-restricted content, web scraping, or other purposes.
Remember that the “best” proxy server varies depending on your specific requirements. The key is to carefully evaluate your needs, the features offered, and the reputation of the proxy provider to make an informed decision.
Recommended articles:
How to setup a proxy server? 3 main types of proxy server & setup process.
8 Interesting Myths About Virtual Private Networks – VPN.
What is the Advanced Encryption Standard (AES)? All You Need to Know.
15 most important cyber security tips for business.
What is cyber security? All you need to know about cyber security.