Proxies are used for a variety of reasons from where I will discuss the main 12 reasons behind the use of a proxy. The purposes of using proxy can range from enhancing security and privacy to optimizing network performance and access to web content.
Here in this post I will discuss about why a proxy is being used. Let’s see the main 12 reasons of the use of a proxy.
Main 12 Use of a Proxy
I already have given a summery of why a proxy is being used. Now it’s the time to see why a proxy is used in different purpose in details.
Proxies serve a variety of purposes and have several practical uses across different domains. Let’s see in details about the use of proxy.
1. Anonymity and Privacy
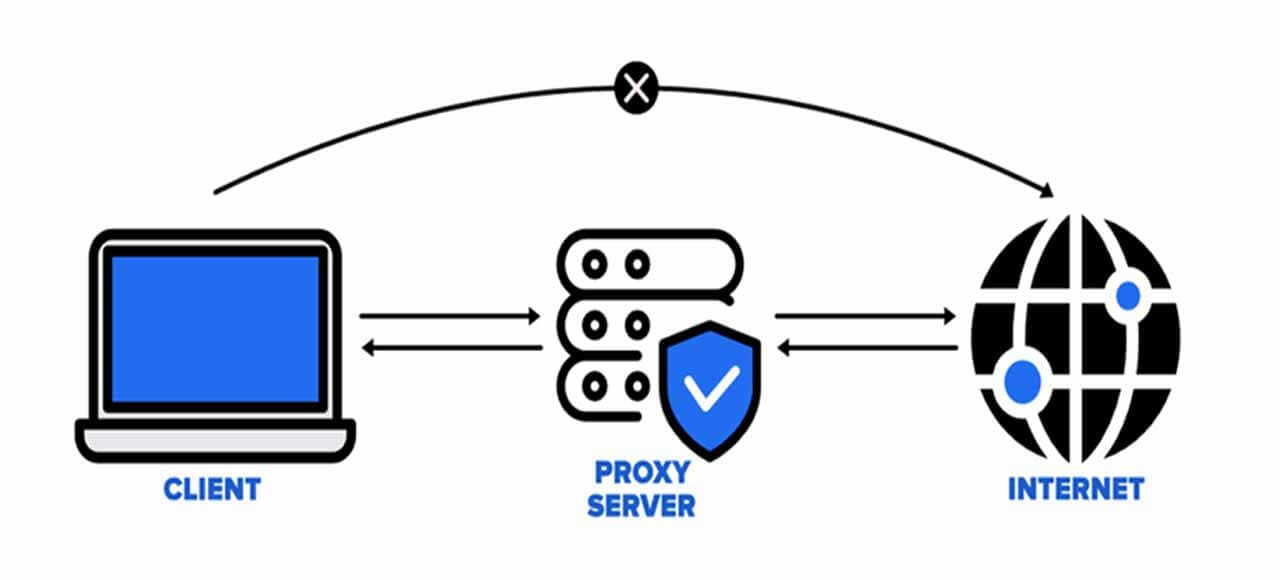
Probably the main reason to use of a proxy is anonymity and privacy given by a proxy. Proxies can mask your IP address, making it more difficult for websites and online services to track your online activities. This helps protect your privacy and maintain anonymity.

Proxies can enhance anonymity and privacy to varying degrees, depending on the type of proxy and how it’s configured. Here’s a breakdown of how proxies can affect anonymity and privacy:
Transparent Proxies don’t hide your IP address. Websites and online services can see your actual IP address. They are primarily used for caching and content filtering, not for anonymity.
Anonymous Proxies hide your IP address from the target server, providing a basic level of anonymity. However, they may still reveal some information about you.
High-Anonymous Proxies provide the highest level of anonymity. They don’t disclose your IP address to the target server, making it more challenging to trace your online activities.
Virtual Private Networks (VPNs) and Socks proxies are often used to maximize anonymity. They route your traffic through servers located in various regions, obscuring your IP address and encrypting your data.
VPNs, in particular, offer strong privacy and security by encrypting your entire internet connection, protecting your data from eavesdropping.
See also: 15 things to consider when choosing a proxy.
When using a proxy for privacy, it’s essential to trust the provider. The proxy server operator can potentially log your activities or access your data. Ensure that you choose a reputable and trustworthy provider.
Proxies can introduce some privacy risks if not configured properly or used with caution. For instance, a malicious proxy could intercept and monitor your traffic, potentially compromising your data.
The Tor network is a specialized form of proxy that focuses on providing strong anonymity and privacy. It routes your traffic through a series of volunteer-operated servers, making it extremely challenging to trace your online activities. Tor is commonly used by individuals who require high levels of privacy and anonymity.
The level of anonymity and privacy provided by a proxy depends on how it’s configured. It’s essential to understand the specific settings and capabilities of the proxy you are using.
When connecting to websites, using HTTPS and SSL (Secure Sockets Layer) encryption can help protect your data, even when using a proxy. This encryption ensures that your communication with the website remains secure and private.
2. Access Control
This is also another important use of a proxy. They can restrict or grant access to specific websites or services, allowing organizations to enforce internet usage policies and block access to unwanted or potentially harmful content.

Proxies are instrumental in enforcing access control within networks, offering organizations a robust mechanism to manage and regulate user access to online resources.
Acting as gatekeepers between users and the internet, proxies can restrict or grant access based on predefined policies.
This allows businesses to safeguard sensitive information, control the usage of specific applications or websites, and mitigate potential security risks.
Proxies excel in providing an additional layer of defense against unauthorized access, ensuring that only authenticated and authorized users can access designated resources.
Through granular access controls and logging capabilities, proxies empower organizations to monitor and track user activities, enhancing overall network security and compliance with corporate policies.
3. Content Filtering
Proxies can filter web content, blocking access to websites with malicious or inappropriate content, as well as preventing the download of malware or viruses.

Proxies serve an essential role in content filtering by acting as intermediaries between users and the internet, allowing organizations to manage and control the types of content that can be accessed.
Through predefined policies, proxies can block or allow access to specific websites or content categories, helping businesses enforce acceptable use policies, enhance security, and comply with regulatory requirements.
Content filtering proxies are adept at screening out malicious websites, preventing access to inappropriate or non-business-related content, and reducing the risk of malware infections.
By implementing content filtering, organizations can optimize bandwidth usage, improve network performance, and maintain a secure and productive online environment for users within their network.
4. Bypassing Geographical Restrictions
Some proxies, particularly those known as geo-proxies, can help users access content that is geo-blocked or regionally restricted by routing their traffic through servers in different countries.
Bypassing geographical restrictions can be one of the important reason about the use of a proxy today.
5. Load Balancing
Proxies can distribute incoming network traffic across multiple servers to ensure even load distribution and prevent server overload, which improves system reliability and performance.
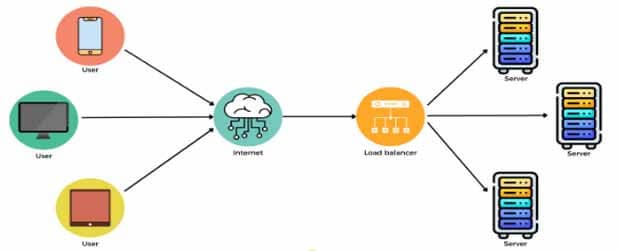
6. Caching
Proxies can cache frequently accessed data, reducing the need to fetch the same data from the internet repeatedly. This saves bandwidth and speeds up content delivery.
As internet user rises day by day, we need to find necessary data instantly which feature is provided by a proxy. For this reason we can’t avoid the use of a proxy to speed up browsing experience.
7. Security
Proxies can act as an additional layer of defense by filtering out malicious traffic, blocking attacks, and inspecting incoming and outgoing data for security threats.
See also 15 most important cyber security tips for business.
In this 21’s century, security is becoming our main concern day by day. Obviously a proxy can enhance security of your data and protect you from various infections.
By using a proxy you can safe your personal data effectively which is the another main reason behind the use of a proxy.
8. Performance Optimization
Some proxies can compress data before delivering it to clients, reducing bandwidth consumption and speeding up content delivery. They can also optimize content for specific devices or network conditions.
While sending data, we need to reduce the size of data keeping original data unchanged. This can be done effectively by a proxy.
It reduces your file size by compressing and send it which takes less time to deliver.
9. Monitoring and Logging
Proxies can log network activities, providing administrators with valuable information for troubleshooting, security analysis, and performance monitoring.
The admin can easily monitor the necessary information by seeing the log which is also a main reason of use of a proxy.
10. Business Applications
In business applications, proxies serve various essential functions to enhance security, optimize performance, and enforce access policies. Proxies act as intermediaries between users and external resources, allowing organizations to filter and control internet access, ensuring compliance with security protocols.
They can also improve network performance by caching frequently accessed data, reducing bandwidth usage, and optimizing content delivery. Proxies enable businesses to monitor and log network activities, aiding in troubleshooting and security analysis.
Moreover, in corporate environments, proxies play a pivotal role in enforcing access controls, safeguarding sensitive data, and providing an additional layer of defense against cyber threats.
Whether used for content filtering, load balancing, or securing sensitive communications, proxies contribute significantly to the smooth and secure functioning of business applications within an organizational network.
11. Malware and Virus Scanning
Proxies play a vital role in enhancing cybersecurity by serving as a frontline defense against malware and viruses. Configured to filter web content, proxies block access to known malicious sites and inspect incoming and outgoing traffic for malware signatures.
Employing HTTPS inspection, they decrypt and analyze encrypted traffic, ensuring that even secure connections are scrutinized for potential threats.
Proxies can also scan files downloaded from the internet, integrate real-time threat intelligence feeds, and employ sandboxing techniques to identify and isolate suspicious files.
In the event of a threat detection, proxies can quarantine infected devices, trigger remediation actions, and maintain detailed logs for analysis, providing comprehensive network-wide protection against malicious content and potential cyber threats.
12. Reduced Latency
By caching frequently accessed resources and optimizing data delivery, proxies can reduce latency, providing faster access to web content.
The use of proxies can be quite versatile, and the specific reasons for using them will depend on your needs and goals.
Whether for security, privacy, content access, or network performance, proxies offer a range of solutions to meet various requirements in different contexts. This is another important use of a proxy.
Final Words
In this advanced world technology is advancing with a robust speed. We are getting addressed with a lot of new technology everyday.
Today a proxy helps us to improve the use of each new technology by enhancing a lot of features especially security related things.
I already have discussed the main 12 use of a proxy. I hope you have get a clear idea about the use of a proxy. Feel free to share your experience bellow the comment box.
Recommended articles:
How to setup a proxy server? 3 main types of proxy server & setup process
15 Things To Consider When Choosing A Proxy
Construction of a VPN server diagram
8 Interesting Myths About Virtual Private Networks – VPN
15 most important cyber security tips for business